The concept of attack is nothing new; the advanced approach that industry is taking forward to solve the problem occurring due to it is new. If we talk about old traditional ways of working that won’t stand out anywhere in the market now as the business are coming up on the digital platform very quickly.As digital platforms are helping to grow business rate easily by making it global.
There are thousands of bytes of data that flow in a network within a second.Though the data streaming would be fast but the chances of attacks they rise too.And one of the most occurring and costly attacks that companies are facing is the ransomware attack.
The ransomware attack is coming up as a business model where thousands of organizations get breached and asked for huge amounts of ransom.At an early stage the organization the are much worried for the business growth and they miss out the basic criteria that is essential to draw secure business in long term.Ransomware is not symbolise to have a certain set of step that occur and it is said to be ransomware,Ransomware is a group of malicious activity that occur together to lead final destination where organizations they lose the access of their file data and get encrypted until the ransom is paid.The attackers demand the handsome amount that cost billions.
The ransomware attacks are coming up in the form of chains that does not seem to be in a state of attack progression but actually that is the step vector leading toward the final destination to make it ransomware.
The most observed way through which ransomware comes up is through phishing mail and compromised websites.While surfing them the malicious files or script land up in the user system and initiate its process.
There are various ways and extensions that we usually see the ransomware file has .Some of them are as follows:
.keybtc@inbox_com, .0x0, .bleep, .1999, .vault, .HA3, .toxcrypt, .magic, .SUPERCRYPT, .CTBL, .CTB2, .ecc, .ezz, .exx, .zzz, .xyz, .aaa, .abc, .ccc, .vvv, .xxx, .ttt, .micro, .encrypted, .locked, .crypto, _crypt, .crinf, .r5a, .XRNT, .XTBL, .crypt, .R16M01D05, .pzdc, .good, .LOL!, .OMG!, .RDM, .RRK, .encryptedRSA, .crjoker, .EnCiPhErEd, .LeChiffre, etc.
In the present time many solutions are coming up in a modular approach to provide a solution as per the particular use case requirement, that won’t be a long-term leading solution.
What is required in terms of a solution to overcome these breaches?
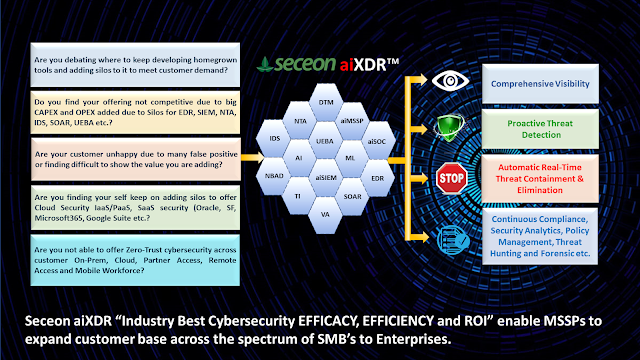
The solution should never be a modular solution providing a solution for a particular set of challenges that are faced by industry ,it should be a proactive solution with 360 degree Comprehensive visibility.The solution should be proactive to mitigate the breach risk in early stages itself rather than going in reactive approach after the breach happens.
The Seceon aiSIEM is a complete raft of automated tools that an IT infrastructure requires to be secured. The solution clutches all the raw log and flow generated by different endpoints and does the data engineering with advanced ML/AI with context and behaviour analysis.
The moment any such malicious activity is found in the system it raises the alert defining its severity and confidence on the basis of what behavioural pattern its follows, it takes the context of any similar event that may have happened in past and does all the correlation to provide accuracy in alerts.With more passing day the solution become more precise and accurate.
The solution is enriched with the capability of push button and auto remediation policy which makes life of an analyst easy by automating it.
To know more about the solution and its outstanding capability visit www.seceon.com and book a demo on the portal.To book a demo Click Here!!
A must look solution before you decide on any security solution in your infrastructure.
No comments:
Post a Comment